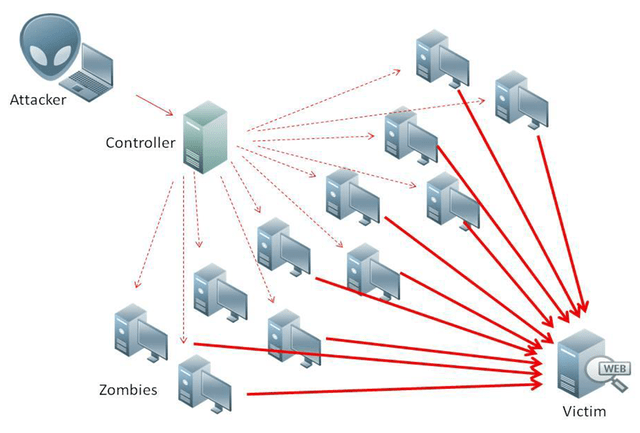
Our story begins with a simple If unsavory news item. As happens every summer, residents of the Faroe Islands joined whalers in the traditional killing of pilot whales and more than 100 dolphins. Local.fo, a Faroese online news magazine, launched the story on September 12, 2018. At noon the next day, a tsunami of fake network traffic engulfed the site. Operations came to a screeching halt, and the attack blocked access to the website for more than six hours.
It was a DDoS attack. Local.fo had been hacked.
Stronger, more frequent, and more dangerous attacks
Local.fo joins a growing list of targets of a cyberattack. These attacks are not the usual, “Hands up, give us your money” approach to hacking. The perps—they call themselves hacktivists—usually don’t want money. They want attention and want to make a statement. Organizations such as Local.fo become targets when they publicize causes, stories or ideas that hacktivists don’t like.
Readily available hacking tools create the perfect opportunity for political grandstanding via cyber-attacks. Hacktivists are using these resources to build more potent attacks and go after a broader range of targets. And now, some hacktivists are moving into outright crime—ransom and data theft.
Changing trends in the digital soapbox
Hacktivists who design politically motivated exploits have a wide variety of methods to choose from. However, three tactics have become standard-issue techniques:
- Denial of service: This approach denies site visitors the use of valuable services and calls attention to the hacktivist’s cause.
- Defacement: Sometimes called internet graffiti, this tactic changes the visual appearance of a site. Hackers take control of a domain and replace website content with propaganda that promotes their cause.
- Doxing: “Dox” is a slang expression for documents. This tactic publicizes private or personal information about hacktivist opponents. The goal: scrape data from digital “documents” to intimidate or embarrass groups, individuals, or causes.
None of these methods is new. But, they’re being used in an environment that promises stronger attacks against a broader range of targets.
Stronger, more complex, and more expensive attacks
Hacktivist exploits that are bigger, more complex, and costlier to defend – these are the current hacktivist trends:
- Stronger attacks. More internet traffic will lead to more powerful DDoS attacks. That’s one likely result of increased internet capacity. New 5G technology will expand internet bandwidth and three-fold increases in speed.
- New targets. Increasingly, local and state government agencies are targets of hacktivist exploits. Agency IT security pros now worry about frozen servers, defaced websites, and stolen data that other hacktivist targets suffer.
However, the impact of these exploits goes far beyond embarrassment. Inactive sites prevent taxpayers from logging on to government websites. No one can get information or conduct business when the system is down. Also, it’s the taxpayers, who must pay the recovery-related operations costs. None of this promotes taxpayer trust in government, which in effect, is an agency’s brand reputation.
- A move into crime. Pedophilia, drug dealing, and embezzlement are just a few examples of the offenses of people outed by hacktivists. Now, some hacktivists are changing their role from reporting crimes to committing them.
Hacktivists usually prefer messaging to money. But some groups take that small step between defacing a website and committing cybercrime or extortion.
The Kerala Cyber Warriors, a hacktivist group, headquartered in India, are a prime example of this trend. They install ransomware in Pakistani servers for “patriotic purposes.” (Translation: they finance their operations with cyber-crime.) The ransomware, named KCW after the group, encrypts the files stored on site. Website owners must then pay a ransom payment to get their files back.
Whether you think hacktivism is a nuisance or a danger, it’s growing. However, IT security pros can take simple measures to minimize the risk and effects of an attack.
The best offense is a good defense
How do you defend against hacktivists? Identify the vulnerabilities they target and secure servers against those threats. Nothing is surprising about the resulting list of defense measures. However, each familiar item adds can strength to security defenses:
- Set up necessary security policies (strong passwords, correct configurations) and enforce them consistently.
- Use web application-level firewalls to filter, monitor, and block malicious traffic.
- Create and follow secure coding standards on all sites.
- Use testing tools to make sure that the code you launch is secure.
- Prevent cybercriminals from exploiting out-of-date software by patching by making updates a standard policy.
- Regularly scan web applications for vulnerabilities.
- Secure vulnerable websites from common hacktivist attacks using multi-layered protection.
Hacktivist attacks are like that proverbial box of chocolates—you never know what you’ll get. However, there are plenty of tools and tried-and-true best practices that can cut the impact when hacktivists come to call.