Hacker Group Turla uses extensions in the Firefox browser to spy on victims. Since 2007 the cyberspionage group Turla has been attacking governments as well as government representatives and diplomats. Now it has added a new tool to its arsenal: European cybersecurity software producer ESET has analyzed a new attack strategy, in which the group uses a Firefox extension to abuse the popular social network Instagram for their purposes.
The tactics of the Turla group are usually the compromise of web pages, which are called more often by the targeted victims – so-called “watering hole attacks”. Once on the net, users are redirected to a command-and-control server (C & C), through which victim device devices can be received and monitored.
Dissemination via Instagram Comments
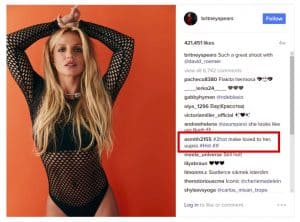
When observing recent Turla campaigns, researchers at ESET – the cybersecurity company noticed a Firefox extension that was recently classified as harmful. Unlike older versions, this extension uses a bit.ly short URL to connect to the C & C server. This URL path is not found in the Firefox extension, but is distributed via the commentary function of individual Instagram posts. for example under a picture on the account of Britney Spears.
To get to the bit.ly URL, the extension scans all Instagram comments. For each comment she calculates, she has a custom hash value. If the hash value matches the number 183, the URL path is pulled from the comment.
Challenge for cybersecurity industry
“The fact that Turla uses Social Media to restore C & C addresses makes it difficult for cybersecurity solutions providers to live with, and this tactic makes malicious traffic on social media channels even more difficult,” said Jean-Ian Boutin , Senior Malware Researcher at ESET. “Because the information for the Command-and-Control URL is hidden in simple comments, the attacker has the ability to easily modify or delete them completely.”
To avoid being a victim of such a watering hole attack, the ESET –
cybersecurity researchers recommend keeping browsers and their extensions up-to-date at all times. In addition, users should download and install extensions and add-ons only from reputable sources. Fortunately, modern cybersecurity solutions are capable of detecting suspicious websites that spread potentially harmful content and warning the user in time.