Introduction to Cybersecurity Certification Roadmap
A Booming Cybersecurity Job Market: Why Now Is the Time
The digital world is expanding. So also the threat landscape does. Every day, businesses, governments, and individuals face increasing risks from cyberattacks, ransomware, phishing schemes, and data breaches. This surge in cyber threats has fueled an unprecedented demand for skilled cybersecurity professionals across various industries.
According to recent job market studies, cybersecurity roles are among the fastest-growing careers in the tech industry. There are over 3.5 million unfilled cybersecurity jobs worldwide. Cybersecurity roles vary from entry-level cybersecurity analysts to senior security architects. The need for qualified experts is expected to grow in the coming years.
Why Cybersecurity Certifications Are Essential for Career Growth
If you are starting out in IT or aiming to transition into a cybersecurity-focused role then having the right credentials can set you apart in a competitive job market. Cybersecurity certifications very much differ from traditional degree programs. Cybersecurity certifications provide a targeted, skills-based approach to learning. They validate your knowledge and expertise in specific areas like network security, penetration testing, cloud security, and risk management.
Certifications also demonstrate to employers that you are committed to continuous learning and industry standards. Many hiring managers now list “cybersecurity certification required or preferred” in job postings. That is for roles like Security Operations Center (SOC) Analyst, Penetration Tester, and Certified Information Systems Security Professional (CISSP).
Some of the most in-demand cybersecurity certifications in 2025 are CompTIA Security+, CEH, CISSP, and CCSP. Each Cybersecurity certification serves as a stepping stone to more advanced roles. Gaining these credentials is often a prerequisite to landing high-paying cybersecurity jobs or moving into leadership roles in IT security.
What This Cybersecurity Certification Roadmap Covers
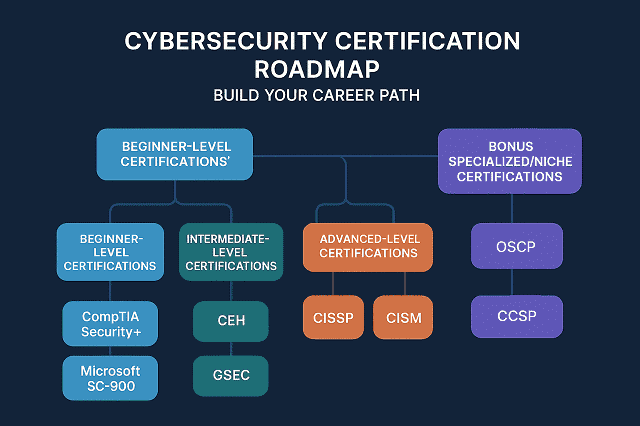
This comprehensive cybersecurity certification roadmap is designed to guide you through every stage of your journey. Prodigitalweb is covering it from cybersecurity certifications for beginners all the way to expert-level cybersecurity credentials.
We will break down the roadmap into three core phases:
- Beginner-Level Certifications – Ideal for newcomers or those switching careers
- Intermediate-Level Certifications – For professionals with some experience in IT or security
- Advanced-Level Certifications – For those ready to specialize, lead teams, or move into executive positions
We will also cover niche and specialized certifications for cloud security, ethical hacking, and risk management to help you carve out a focused career path.
By the end of this guide, you will have a clear, actionable strategy for choosing the best cybersecurity certification path tailored to your goals, experience level, and job market demand.
Understanding Cybersecurity Roles
Before diving deep into certifications, it is important to understand the key cybersecurity roles that exist within the industry. Each job role demands a unique skill set and career focus. Besides, each job role demands most importantly a tailored certification path. This foundational knowledge is vital for anyone looking to build a career in cybersecurity. Further, this understanding ensures your efforts are directed toward the right cybersecurity certification roadmap from day one.
Overview of Key Cybersecurity Job Roles
-
Cybersecurity Analyst
It is often considered the starting point in cybersecurity careers. The Cybersecurity Analyst plays a frontline role in protecting organizations from digital threats.
- Primary Responsibilities:
- Monitoring and analyzing security events
- Detecting and responding to incidents
- Implementing security controls and threat intelligence
- Typical Tools: SIEM (Splunk, IBM QRadar), IDS/IPS, Firewalls, Wireshark
- Industries Hiring: Finance, healthcare, government, retail
Ideal for: Beginners or IT professionals switching to security
Growth Tip: Analysts often progress to SOC roles or security engineering with experience.
-
Penetration Tester (Ethical Hacker)
Pen Testers, or ethical hackers, simulate cyberattacks to identify and exploit vulnerabilities before malicious hackers do.
- Primary Responsibilities:
- Conducting penetration tests and vulnerability assessments
- Exploiting weaknesses in networks, apps, and systems
- Writing detailed technical reports with remediation guidance
- Typical Tools: Kali Linux, Metasploit, Burp Suite, Nmap
- Industries Hiring: Cybersecurity consultancies, Fintech, SaaS companies, and defense contractors
Ideal for: Those passionate about offensive security and problem-solving
Growth Tip: Many pen testers eventually specialize in red teaming or bug bounty programs.
-
Security Engineer
Security Engineers are the architects of an organization’s defense infrastructure. They design, build, and maintain secure systems.
- Primary Responsibilities:
- Creating security architecture and implementing security protocols
- Automating security processes and managing threat mitigation tools
- Ensuring infrastructure aligns with best practices and compliance standards
- Typical Tools: Firewalls, IDS/IPS, scripting tools, EDR platforms, cloud security tools (AWS/GCP/Azure)
Ideal for: Professionals with prior experience in IT, network engineering, or system administration
Growth Tip: This role can branch into specialized domains like DevSecOps or cloud security engineering.
-
Chief Information Security Officer (CISO)
The CISO is the executive leader responsible for an organization’s cybersecurity strategy, risk management, and compliance.
- Primary Responsibilities:
- Defining the overall information security strategy
- Managing teams of analysts, engineers, and managers
- Liaising with executive leadership and regulatory bodies
- Skills Required: Strong leadership, budgeting, risk assessment, policy development, and compliance (ISO, NIST)
Ideal for: Senior professionals with 8–15+ years of experience in security roles
Growth Tip: Most CISOs start as engineers or analysts and build their way up through experience and certifications.
Mapping Certifications to Specific Cybersecurity Roles
To help you align your goals, here is a detailed breakdown of which cybersecurity certifications match which job roles. This mapping forms the core of any effective cybersecurity certification roadmap and serves as a guide for your career planning.
| Role | Relevant Certifications | Career Level | Cert Type |
| Cybersecurity Analyst | CompTIA Security+, Cisco CyberOps Associate, SSCP | Beginner | Foundational |
| Penetration Tester | CEH, OSCP, eJPT, GPEN | Intermediate | Offensive Security |
| Security Engineer | CompTIA CySA+, CASP+, GSEC, Microsoft SC-200 | Mid-Level | Technical/Defensive |
| CISO / Security Manager | CISSP, CISM, CRISC, CCISO | Advanced | Strategic/Executive |
Why Role-Certification Mapping Matters
Choosing the right certification without understanding your target role is like navigating without a map. For example:
- An aspiring Penetration Tester may waste time on broad managerial certifications like CISM, which will not serve their goals.
- A future CISO who skips CISSP may struggle to prove credibility in leadership roles.
That is why this role-to-certification mapping is a cornerstone of any strategic cybersecurity certification path. It ensures that your time, money, and effort are invested wisely.
Pro Tip:
Let us start by identifying the cybersecurity role that excites you the most. Then build a learning and certification roadmap around it. Combine hands-on lab experience, study guides, and practical projects to reinforce your skills.
Phase 1: Beginner-Level Certifications Roadmap
Laying the Groundwork for Your Cybersecurity Career
Starting your cybersecurity journey can feel overwhelming with the abundance of certifications and learning paths. Phase 1 of the Cybersecurity Certification Roadmap focuses on those who are either new to the tech world or transitioning into cybersecurity from a non-technical background. These certifications provide the foundational cybersecurity knowledge that prepares you for real-world roles and advanced learning tracks.
Who Should Start Here?
This phase is ideal for:
- High school students exploring IT and cybersecurity career paths
- College students pursuing degrees in computer science or information technology
- Fresh graduates aiming for entry-level cybersecurity jobs
- Career switchers transitioning from unrelated fields like education, law, or retail
- IT professionals like help desk or network support staff entering the cybersecurity domain
Top Beginner Cybersecurity Certifications
These certifications are recognized by industry leaders. These provide strong ROI in terms of job access and foundational skill building.
-
CompTIA IT Fundamentals (ITF+)
Purpose: To introduce complete beginners to essential IT and security concepts. It is an entry-level cybersecurity course.
- Topics Covered: Hardware basics, software, operating systems, databases, and basic cybersecurity principles
- Recommended For: Absolute beginners, students in high school or early college
- Duration to Complete: 2–4 weeks with self-paced learning
Why It is Important:
It answers the fundamental question: “Is IT or cybersecurity right for me?” The certification provides clarity before committing to more technical and costly paths.
-
CompTIA Security+
Purpose: CompTIA Security+ acts as a launchpad into core cybersecurity practices. It is often a job requirement for entry-level positions.
- Topics Covered: Risk management, threat analysis, secure network architecture, identity and access control, cryptography
- Globally Recognized: Meets U.S. Department of Defense 8570 compliance
- Recommended For: Career changers, junior IT staff, self-learners targeting security analyst roles
- Exam Duration: 90 minutes
Why It is Important:
Security+ is often cited as the #1 certification in entry-level cybersecurity job postings. CompTIA Security+ is vendor-neutral. That means it applies across tools, platforms, and industries.
-
Microsoft SC-900: Security, Compliance, and Identity Fundamentals
Purpose: Microsoft SC-900 offers a cloud-centric introduction to cybersecurity, compliance frameworks, and identity governance. This is especially true in Microsoft ecosystems.
- Topics Covered: Microsoft Azure and Microsoft 365 security, zero trust principles, compliance controls, access governance
- Recommended For: Professionals interested in cloud security, Microsoft platforms, or Azure security roles
- Learning Path: Available for free through Microsoft Learn
Why It is Important:
In a world rapidly shifting to cloud-based infrastructure, understanding Microsoft’s security ecosystem can open paths to cloud security analysts, compliance officers, or identity administrator roles.
Core Skills You Will Develop in Phase 1
If you pursue one or all of the certifications above then you will start acquiring real-world, job-ready skills such as:
- Basic networking and system security fundamentals
- Understanding cyber threats, vulnerabilities, and exploits
- How to recognize social engineering attacks (like phishing and baiting)
- Risk identification and simple mitigation strategies
- Working knowledge of security policies, tools, and compliance frameworks
- Familiarity with incident reporting, firewall configuration, and user authentication
These are the building blocks for nearly all cybersecurity career paths both technical and managerial.
Career Opportunities Unlocked by Beginner Certifications
Beginner certifications help demonstrate industry-aligned knowledge and practical problem-solving skills. They also enable you to compete for entry-level roles in a highly competitive space.
Here are some potential job roles and salary ranges (varies by location and experience):
| Job Role | Salary Range (USD) | Recommended Certifications |
| Cybersecurity Intern | $30,000 – $45,000 | ITF+, SC-900 |
| IT Support Specialist | $45,000 – $55,000 | ITF+, Security+ |
| Junior Security Analyst | $55,000 – $70,000 | Security+, SC-900 |
| SOC Analyst (Tier 1) | $60,000 – $75,000 | Security+, SC-900 |
| Risk Analyst Assistant | $50,000 – $65,000 | SC-900, Security+ |
Tip: Employers increasingly value certifications even for non-technical cybersecurity roles like compliance monitoring, identity governance, and risk documentation.
How to Approach Phase 1 Strategically
Here is how to make the most of this phase in your cybersecurity certification roadmap:
- Choose one foundational certification to begin—ITF+ if you are brand new, or Security+ if you already know basic IT.
- Use structured learning platforms such as LinkedIn Learning, Cybrary, Microsoft Learn, or Udemy.
- Get hands-on experience through labs and simulations (TryHackMe, Hack The Box Beginner Path).
- Join cybersecurity communities for mentorship (Reddit’s r/cybersecurity, Discord groups, and local meetups).
- Pair certification with personal projects—create a home lab or document your learning in a GitHub portfolio.
Laying a Strong Foundation
Phase 1 is not just a checklist, it is a mindset shift. Earn your first entry-level cybersecurity certification to demonstrate a commitment to learning and a grasp of fundamental security principles. Phase 1 is a solid platform for advancing through the Cybersecurity Certification Roadmap.
The next step is to move forward with Phase 2: Intermediate-Level Certifications. In Phase 2 you can start specializing based on your interests—defensive security, ethical hacking, or cloud security.
Phase 2: Intermediate-Level Certifications Roadmap
A Critical Step in Your Cybersecurity Certification Roadmap
Once you have built a strong foundation through beginner-level credentials. The next logical step in the Cybersecurity Certification Roadmap is acquiring intermediate certifications. These certifications validate your ability to solve real-world cybersecurity challenges and showcase your readiness for more specialized roles.
This phase is about transforming your theoretical knowledge into practical, job-ready skills that align with industry expectations.
Ideal for: Professionals with 1–3 Years of Experience
The intermediate stage targets individuals who have:
- Gained hands-on exposure through entry-level roles like help desk technician or junior security analyst.
- Completed basic certifications like CompTIA Security+ or Microsoft SC-900.
- Worked in adjacent fields like network administration, system support, or IT operations.
If you are someone aiming to move from a support role to a proactive defense or analysis role then this is where you build credibility.
Top Intermediate-Level Certifications to Consider
Here are three key certifications that serve as career accelerators in your cybersecurity journey.
-
Cisco Certified CyberOps Associate
Overview:
This Cisco certification targets aspiring security operations center (SOC) analysts. CyberOps Associate teaches how to monitor, detect, and respond to cybersecurity incidents in enterprise environments.
Core Domains Covered:
- Security monitoring using SIEM systems (Splunk)
- Understanding security concepts and common attack vectors
- Endpoint security, firewalls, and IDS/IPS systems
- Incident response procedures
Skills You Gain:
- Log analysis and event correlation
- Network intrusion detection and escalation protocols
- Recognizing and handling malware infections
- Understanding SOC processes and layered defense strategies
Ideal Job Roles:
- SOC Analyst (Tier 1 or Tier 2)
- Security Operations Analyst
- Junior Threat Hunter
Why It Matters:
CyberOps Associate is one of the best intermediate cybersecurity certifications for blue-team roles and a stepping stone toward more advanced Cisco credentials.
-
Certified Ethical Hacker (CEH)
Overview:
Certified Ethical Hacker (CEH) is offered by EC-Council, CEH. It is globally recognized and focuses on offensive security. It teaches how to legally hack into systems to discover vulnerabilities before attackers do.
Core Domains Covered:
- Footprinting and reconnaissance
- Scanning networks and system hacking
- Web application attacks and SQL injections
- Wireless, mobile, and IoT hacking
- Social engineering and malware threats
Skills You Gain:
- Simulating real-world cyberattacks using Kali Linux and Metasploit
- Understanding how attackers exploit system weaknesses
- Conducting vulnerability assessments and penetration tests
- Writing basic exploits and scripts
Ideal Job Roles:
- Ethical Hacker
- Penetration Tester
- Red Team Analyst
- Security Consultant
Why It Matters:
CEH is often a required or preferred credential for pen-testing roles and is included in many job listings for offensive cybersecurity positions.
-
GIAC Security Essentials (GSEC)
Overview:
Offered by the SANS Institute through GIAC. GSEC is highly respected and bridges the gap between foundational knowledge and advanced topics in cybersecurity.
Core Domains Covered:
- Active defense and incident handling
- Access controls, cryptographic principles
- Linux/Windows command-line usage for security
- Network security technologies
- Secure communications and authentication
Skills You Gain:
- Defensive strategies using both host-based and network-based controls
- Hands-on experience with security tools like tcpdump, Wireshark, and Netcat
- Identifying suspicious behavior in logs and packet captures
- Implementing best practices for secure system configurations
Ideal Job Roles:
- Security Administrator
- Information Security Analyst
- Risk Analyst
- Compliance Officer
Why It Matters:
GSEC is widely accepted in the federal and defense sectors and is one of the most well-rounded cybersecurity certifications for professionals. It is focused on practical skills and real-world application.
Real-World Applications and Career Progression
Intermediate certifications enable professionals to move from theoretical understanding to real-time, hands-on application in dynamic environments.
Roles Unlocked at This Stage:
| Position | Estimated Salary (US) | Relevant Certifications |
| SOC Analyst (Tier 2) | $80,000 – $95,000 | Cisco CyberOps, CEH |
| Cybersecurity Analyst | $85,000 – $105,000 | GSEC, CEH |
| Penetration Tester | $90,000 – $115,000 | CEH, GSEC |
| IT Security Specialist | $95,000 – $120,000 | CyberOps, GSEC |
Examples of Real-World Use Cases
- SOC Analyst Scenario
- You are monitoring SIEM dashboards to detect anomalies in network traffic. Using your knowledge from Cisco CyberOps, you identify a brute-force login attempt and trigger the organization’s response protocol.
- Penetration Tester Engagement
- You are tasked with conducting a vulnerability assessment for a retail company’s website. With skills from CEH, you exploit outdated plugins and prepare a remediation report for the client.
- Compliance and Security Auditing
- You are part of a risk management team using GSEC knowledge to perform a company-wide security audit—analyzing password policies and reviewing access controls. You need to ensure compliance with standards like ISO/IEC 27001.
Why Phase 2 Is a Game-Changer in Your Cybersecurity Certification Roadmap
- Positions you as a hands-on professional ready to handle critical infrastructure and security issues
- Helps shift from support roles to proactive cybersecurity functions
- Acts as a launchpad for advanced certifications like CISSP, OSCP, and CISM
- Validates your knowledge across defensive and offensive security operations
Key Takeaways:
- These certifications build job-ready cybersecurity skills required by today’s employers.
- They prepare you to work in complex environments and take ownership of incident response or security testing tasks.
- They significantly improve your chances of landing higher-paying roles and moving up the cybersecurity ladder.
Phase 3: Advanced-Level Certifications Roadmap for Leadership
Commanding the Cybersecurity Landscape with Strategy and Expertise
Once you have conquered the basics and built a robust intermediate skill set, it is time to move to Phase 3 of your cybersecurity journey. This is where you transition from a doer to a decision-maker. Advanced-level certifications validate your technical proficiency. In addition, it also validates your capability to influence, lead, and secure enterprise-wide environments.
If you aim to become a CISO, Security Architect, or Compliance Lead then this phase sharpens your ability to make strategic security decisions that affect organizations at a structural level.
Who Should Pursue Advanced-Level Certifications?
This stage is not for beginners. It is tailored for:
- Professionals with 5–10+ years of hands-on cybersecurity experience
- Those who have already earned intermediate certifications like CompTIA Security+, CySA+, or SSCP
- Individuals managing or leading cybersecurity teams
- Professionals preparing for roles in security governance, architecture, and compliance
You have likely been involved in designing or implementing security policies. In addition, you have to be involved in managing incident response teams or contributing to enterprise-level security strategies.
Why Advanced Certifications Matter
Validate Your Strategic Thinking
Employers need professionals who can think beyond tools and tactics. They do prefer those who can align security initiatives with business objectives.
Gain Global Recognition
Certifications like CISSP and CISM are recognized worldwide and often listed as mandatory in senior-level job descriptions.
Increase Earning Potential
These certifications are associated with six-figure salaries and executive roles. They elevate your marketability to organizations of all sizes.
Stand Out in the Talent Pool
With demand outpacing supply for senior cybersecurity roles, holding a reputable advanced certification is a game-changer.
Top Advanced-Level Cybersecurity Certifications
-
CISSP – Certified Information Systems Security Professional
Authority: ISC²
Reputation: Globally acknowledged as the flagship cybersecurity management certification
What It Covers:
CISSP is ideal for professionals who want to design, implement, and manage a comprehensive cybersecurity program.
Core Domains:
- Security & Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication & Network Security
- Identity & Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
CISSP Key Benefits:
- Offers a balanced blend of technical and managerial skills
- Required for many CISO and Security Director roles
- Demonstrates your ability to think holistically about security
- Satisfies the DoD 8570/8140 requirements
Ideal Roles:
- Chief Information Security Officer (CISO)
- Information Security Manager
- Security Governance Officer
- Enterprise Security Consultant
Real-World Example:
An energy firm undergoing digital transformation relies on a CISSP-certified professional to design a multi-layered defense strategy across hybrid cloud environments.
-
CISM – Certified Information Security Manager
Authority: ISACA
Focus: Risk, compliance, and governance
What It Covers:
CISM is tailored for professionals managing and auditing enterprise information security programs.
Domains:
- Information Security Governance
- Risk Management
- Security Program Development and Management
- Incident Response and Recovery
Key Benefits:
- Focuses heavily on aligning security with business goals
- Ideal for compliance-heavy industries (finance, healthcare, etc.)
- Sought after by auditors, policy-makers, and GRC experts
- Often a prerequisite for regulatory oversight positions
Ideal Roles:
- Risk and Compliance Manager
- Cybersecurity Program Director
- IT Audit Officer
- Information Assurance Consultant
Real-World Example:
A CISM-certified professional leads the PCI-DSS and HIPAA compliance efforts for a large hospital network. Further, it mitigates regulatory penalties and data breach risks.
-
CASP+ – CompTIA Advanced Security Practitioner
Authority: CompTIA
Focus: Hands-on enterprise-level technical skills
What It Covers:
CASP+ is designed for senior professionals who prefer technical mastery over managerial paths.
Domains:
- Security Architecture
- Governance, Risk & Compliance
- Security Operations
- Integration of Enterprise Security Solutions
Key Benefits:
- The only performance-based certification at the advanced level
- Focuses on solution implementation and complex troubleshooting
- Covers hybrid environments, cloud security, cryptography, and zero-trust models
- Preferred by technical leads, senior security engineers, and infrastructure architects
Ideal Roles:
- Enterprise Security Engineer
- SOC Manager
- Technical Security Lead
- Cybersecurity Consultant
Real-World Example:
In a government contract scenario, a CASP+ certified engineer leads the deployment of an endpoint detection and response (EDR) system across a multi-site infrastructure. It ensures both security and performance.
Roles These Certifications Can Unlock
| Job Role | Average Salary (US) | Ideal Certification(s) |
| Chief Information Security Officer (CISO) | $180,000 – $250,000+ | CISSP, CISM |
| Security Program Manager | $120,000 – $160,000 | CISM, CASP+ |
| Enterprise Security Architect | $130,000 – $190,000 | CISSP, CASP+ |
| IT Risk & Compliance Manager | $110,000 – $150,000 | CISM, CISSP |
| Cybersecurity Consultant | $100,000 – $160,000 | Any Advanced-Level |
These certifications influence your salary. In addition, these certifications also grant you authority and credibility in client-facing and executive board scenarios.
Real-World Scenarios That Show Their Value
- Executive-Level Planning: A CISSP professional creates a cybersecurity roadmap that aligns with a $100M SaaS product’s development and global expansion plans.
- Regulatory Oversight: A CISM-certified manager ensures an insurance firm meets ISO 27001 standards. It is reducing audit failures by 60%.
- Technical Leadership: A CASP+ holder leads a team in securing a hybrid data center using zero-trust architecture. That is thwarting advanced persistent threats (APT).
How to Choose the Right One
| If You Want To… | Go For |
| Lead security strategy at the organizational level | CISSP |
| Oversee governance, audits, and compliance | CISM |
| Stay in hands-on technical security roles | CASP+ |
| Prepare for CISO or executive-level leadership | CISSP + CISM |
Cert Stacking Tip
To stand out even further, many professionals combine advanced certifications:
- CISSP + CISM = Strategic + Governance Mastery
- CISSP + CASP+ = Managerial + Technical Excellence
- CISM + CASP+ = Risk Control + Engineering Precision
This dual approach creates a T-shaped skillset. The dual approach offers a broad managerial vision with deep technical roots.
Key Takeaways
- Phase 3 is where cybersecurity becomes strategic.
- These certifications are milestones for professionals aspiring to influence boardroom decisions and manage global security programs.
- If you lead teams or engineer systems then these credentials offer credibility, career mobility, and global recognition.
Comparison of CISSP vs CISM vs CASP+
| Feature / Aspect | CISSP | CISM | CASP+ |
| Issued By | ISC² | ISACA | CompTIA |
| Focus Area | Broad security management & architecture | Governance, risk, compliance | Hands-on technical implementation at enterprise scale |
| Ideal For | Security leaders, architects, CISOs | Compliance officers, risk managers, audit leads | Senior engineers, SOC leads, technical security experts |
| Experience Required | 5+ years (with endorsement) | 5+ years in information security management | 5–10 years technical experience |
| Exam Format | 125–175 questions (CAT format), 4 hours | 150 multiple choice, 4 hours | 90 performance-based and multiple-choice, 165 mins |
| Cost | ~$749 USD | ~$575 USD (ISACA members), ~$760 non-members | ~$494 USD |
| Key Domains Covered | Risk management, IAM, architecture, operations | Risk, governance, program development | Risk, enterprise security, cryptography, integration |
| Managerial vs. Technical | 60% managerial / 40% technical | 90% managerial / 10% technical | 30% managerial / 70% technical |
| Preferred Industries | Finance, healthcare, government, SaaS | Healthcare, banking, insurance, and compliance-heavy fields | DoD, military, critical infrastructure, hybrid IT orgs |
| Global Recognition | Very high (DoD 8570 recognized) | High (especially in compliance & audit circles) | Medium to high (recognized in defense and technical organizations) |
| Common Career Paths | CISO, Security Director, Security Architect | InfoSec Manager, GRC Lead, Audit Head | Sr. Security Engineer, Technical Consultant, SOC Manager |
| Best For | Becoming a CISO or enterprise-level strategist | Driving compliance, audit, and security program mgmt. | Leading technical defense at the infrastructure level |
Bonus: Specialized/Niche Certifications Roadmap
(Maximizing Your Cybersecurity Certification Roadmap for Career Precision)
The cybersecurity industry is maturing now. It no longer demands generalists alone; it now increasingly values niche experts with deep domain knowledge. Whether, it is ethical hacking, cloud infrastructure protection, or enterprise risk governance, companies are actively recruiting professionals with targeted cybersecurity certifications. Cybersecurity certifications demonstrate specific, high-demand skills.
This bonus phase in your Cybersecurity Certification Roadmap is dedicated to seasoned professionals looking to sharpen their competitive edge and command higher salaries, strategic roles, or even consulting opportunities.
-
OSCP – Offensive Security Certified Professional
What It Is:
The OSCP (Offensive Security Certified Professional) is considered the gold standard for penetration testers. Most certifications rely heavily on theoretical knowledge. However, OSCP is entirely hands-on and practical-exam based. Candidates must identify and exploit real-world vulnerabilities in a controlled lab environment. That is proving not only what they know, but what they can actually do.
Why It Matters:
- Demonstrates deep technical proficiency
- Favored by employers who need a red team or offensive security specialists
- Required or preferred in government, defense, and security consultancy
Advanced Skills Gained:
- Manual vulnerability identification and exploitation
- Buffer overflows and exploit writing
- Bypassing firewalls and AV systems
- Post-exploitation techniques (privilege escalation, persistence)
- Writing custom scripts (Python, Bash) for attacks
Job Roles Unlocked:
- Advanced Penetration Tester
- Red Team Operator
- Exploit Developer
- Security Assessment Consultant
- Threat Simulation Analyst
-
CCSP – Certified Cloud Security Professional
What It Is:
With the rise of cloud-native infrastructures, cloud security has become a priority for every organization. The CCSP by (ISC) ² is one of the most recognized cloud security certifications in the world. CCSP is focused on securing cloud environments and ensuring data integrity across multiple platforms like AWS, Azure, and Google Cloud.
Why It Matters:
- Highly relevant in today’s multi-cloud enterprise architectures
- Prepares professionals to design and implement secure cloud infrastructures
- Helps bridge the knowledge gap between traditional IT security and cloud-native technologies
Advanced Skills Gained:
- Cloud application security (DevSecOps principles)
- Cloud identity and access management (IAM)
- Data lifecycle security in cloud environments
- Cloud compliance frameworks (ISO 27017, NIST, CSA STAR)
- Virtualization and container security
Job Roles Unlocked:
- Cloud Security Architect
- Cloud Risk Analyst
- DevSecOps Engineer
- SaaS Security Consultant
- Multi-cloud Security Analyst
-
CRISC – Certified in Risk and Information Systems Control
What It Is:
CRISC (Certified in Risk and Information Systems Control) by ISACA is a globally respected certification. Certified in Risk and Information Systems Control aimed at professionals in IT governance, compliance, and enterprise risk management. It emphasizes identifying, evaluating, and managing IT risks while designing control systems aligned with business goals.
Why It Matters:
- GRC (Governance, Risk, Compliance) is vital for regulated industries (banking, healthcare, fintech)
- Bridges the gap between technical IT professionals and executive decision-makers
- Enhances credibility in audit, consulting, or policy-making roles
Advanced Skills Gained:
- Enterprise risk identification and assessment
- Designing and monitoring IS controls
- Integration of cybersecurity into corporate governance
- Aligning business strategy with risk tolerance
- Compliance and regulatory framework management (GDPR, HIPAA, SOX)
Job Roles Unlocked:
- IT Risk Manager
- GRC Officer
- Information Assurance Consultant
- Internal Auditor – Cybersecurity
- CISO in compliance-focused organizations
Who Should Pursue These Niche Certifications?
These advanced, specialized certifications are best suited for:
- Experienced cybersecurity professionals ready to specialize
- Those with existing certifications like CISSP, Security+, or CEH
- Career switchers from IT, networking, or audit fields who want to enter high-demand verticals
- Professionals aiming for higher salaries, global roles, or freelance consulting in niche areas
Pro Tip: Align Your Niche Certs with Career Goals
| If You Want to… | Then Consider… |
| Master hands-on hacking & red teaming | OSCP |
| Become a cloud security architect | CCSP |
| Lead GRC and audit in enterprise setups | CRISC |
| Work in government or military security | CASP+ or OSCP |
| Start a consulting firm in niche domains | Any of the above + experience |
Adding specialized certifications to your Cybersecurity Certification Roadmap is not only a resume booster; it is a career game-changer. These credentials are powerful signals to employers, clients, and peers that you are an expert in your domain and not just a generalist. In an industry that is as fast-evolving and competitive as cybersecurity, being niche is being smart.
Comparison Table OSCP vs CCSP vs CRISC:
| Feature/Criteria | OSCP (Offensive Security Certified Professional) | CCSP (Certified Cloud Security Professional) | CRISC (Certified in Risk and Information Systems Control) |
| Domain Focus | Penetration Testing & Ethical Hacking | Cloud Security Architecture & Compliance | IT Risk Management & Governance |
| Issued By | Offensive Security | (ISC)² | ISACA |
| Ideal For | Red Teamers, Pen Testers, Security Researchers | Cloud Security Architects, DevSecOps Engineers | GRC Analysts, IT Risk Officers, Auditors |
| Experience Level | Advanced (Hands-on skills required) | Intermediate to Advanced | Mid to Senior Level |
| Exam Format | 24-hour hands-on practical lab + report | Multiple-choice exam (175 Qs, 4 hrs) | Multiple-choice exam (150 Qs, 4 hrs) |
| Skills Gained | Vulnerability exploitation, manual hacking, scripting | Cloud IAM, security design, data lifecycle mgmt | Risk assessment, control implementation, compliance mgmt |
| Prerequisites | Strong Linux, networking, and scripting knowledge | 5 years IT experience (1 in cloud security) | 3 years of risk/control experience (1 in 2 CRISC domains) |
| Renewal Cycle | Every 3 years (CP credits) | Every 3 years (CPE credits) | Every 3 years (CPE credits) |
| Global Recognition | High among red teams, ethical hackers | Highly respected for multi-cloud security roles | Preferred in governance/audit roles in regulated industries |
| Cost Range | ~$1500 (includes lab time) | ~$599 + annual maintenance fees | ~$575 member / ~$760 non-member |
Tips to Navigate Your Certification Path
Choosing the right path in cybersecurity can feel overwhelming with the vast number of certifications available today. Whether you are just getting started or looking to transition into a specialized role, having a well-thought-out strategy is primary to making progress. In this section of your Cybersecurity Certification Roadmap, we break down actionable tips to help you navigate your journey confidently and effectively.
Set Clear Career Goals
Before you even start studying for your first exam, ask yourself: “Where do I want to be in 3 to 5 years in the cybersecurity field?”
Cybersecurity is a vast industry encompassing roles like:
- Security Analyst
- Penetration Tester
- Security Engineer
- Cloud Security Architect
- CISO or Security Manager
- Risk and Compliance Analyst
Setting clear goals will help you identify the right cybersecurity certifications that align with your long-term vision. For example, aspiring pen testers should consider certifications like OSCP or CEH, while future CISOs might pursue CISM or CISSP.
Choose Certifications Aligned with Your Desired Role
Not all certifications are equal. Some are more tailored to specific job functions than others. Use this cybersecurity certification roadmap to choose wisely:
- Network Defense or SOC Roles: Start with CompTIA Security+ and move to Cisco CyberOps Associate or CySA+.
- Offensive Security: Consider CEH, followed by OSCP.
- Governance/Risk/Compliance (GRC): Begin with CRISC, then pursue CISM.
- Cloud Security: Start with SC-900, then aim for CCSP.
This role-based approach avoids unnecessary detours. And that will ensure each certification adds value to your targeted career path.
Time and Cost Considerations
Some cybersecurity certifications demand significant time and financial investment. Some others offer quick wins. Here is how to assess what fits your schedule and budget:
| Certification | Approx. Study Time | Exam Fee |
| CompTIA Security+ | 2–3 months | ~$392 |
| CEH | 3–4 months | ~$950 |
| CISSP | 4–6 months | ~$749 |
| OSCP | 3–6 months (lab-intensive) | ~$1500 |
Pro Tip: Plan your study schedule around work/life balance and identify free or low-cost learning resources. Scholarships and employer reimbursement programs are often available for well-known certifications.
Combine Self-Learning + Hands-on Labs + Courses.
To succeed in cybersecurity, theory alone is not enough. The best candidates complement their knowledge with real-world simulations and labs.
Self-learning platforms:
- Cybrary
- YouTube channels (NetworkChuck, Professor Messer)
- Official certification books and whitepapers
Hands-on labs:
- TryHackMe (perfect for beginners and pen testers)
- Hack The Box (for advanced penetration testing)
- RangeForce, Immersive Labs, or Boson Labs (for blue team skills)
Courses and Bootcamps:
- SANS training (for GSEC and advanced certs)
- LinkedIn Learning and Udemy (affordable and beginner-friendly)
- Offensive Security Academy (for OSCP prep)
This blended approach ensures you gain both conceptual knowledge and practical skills. These are the two pillars that recruiters actively seek.
Follow these expert tips and reference a detailed Cybersecurity Certification Roadmap, you can craft a career trajectory that is intentional, rewarding, and resilient in the face of industry changes. Align your certifications with clear goals. Be mindful of your time and resources, and always prioritize hands-on learning.
Certification vs Degree: Which is Better?
In a competitive job market, aspiring cybersecurity professionals often ask:
“Should I earn a cybersecurity certification or pursue a degree?”
The truth is, that both paths are valid and can be part of your personalized cybersecurity certification roadmap. However, each comes with its own set of benefits, costs, and use cases. Understanding the difference can help you align your cybersecurity learning path with your career aspirations, whether you are aiming to become a penetration tester, security engineer, or CISO.
When to Choose One Over the Other
When to Choose Cybersecurity Certifications
Cybersecurity certifications are career-focused credentials designed to validate specific technical skills. They are ideal for professionals who want to:
- Break into cybersecurity quickly without spending years in college
- Gain recognition from employers in as little as 3–6 months
- Prove hands-on expertise in niche areas like ethical hacking, SOC analysis, or cloud security
- Switch careers from IT, networking, or software development to cybersecurity
Examples of certifications on the cybersecurity certification roadmap for beginners and intermediates:
- CompTIA Security+ – A foundational certificate recognized globally
- Certified Ethical Hacker (CEH) – Perfect for aspiring penetration testers
- Cisco CyberOps Associate – Focused on SOC operations and incident response
- Microsoft SC-900 – Great for understanding identity and compliance in the cloud
Certifications are also ideal if you are targeting vendor-specific roles, like becoming a Microsoft security analyst, Cisco network security engineer, or AWS cloud security architect.
When to Choose a Cybersecurity Degree
A cybersecurity degree, whether at the bachelor’s or master’s level, offers comprehensive academic training and a broader view of security concepts. You might consider this path if:
- You are just entering the workforce and want a solid, accredited qualification
- You aim to become a security architect, policy advisor, or CISO
- You are applying for jobs in government agencies, defense sectors, or large enterprises that require formal education
- You are planning a long-term career in research, policy, or cybersecurity governance
Popular degree programs include:
- Bachelor’s in Cybersecurity or Computer Science
- Master’s in Information Assurance or Cybersecurity Management
- Online cybersecurity degrees tailored for working professionals
Pro tip: A cybersecurity degree is also more beneficial if you are interested in theoretical concepts, legal frameworks, or project management in cybersecurity—areas that certifications might not cover in depth.
Can They Complement Each Other?
Yes—and in fact, the best cybersecurity professionals often have both.
Think of a cybersecurity degree as the foundation and certifications as the specialized tools you add to your toolkit over time.
Cybersecurity Degree vs Cybersecurity Certification Table
Let us break down how they complement one another:
| Cybersecurity Degree | Cybersecurity Certifications |
| Offers broad academic grounding and theory | Offers focused, practical skills in real-world security scenarios |
| Takes 2–4 years to complete | Takes weeks to months depending on the level and provider |
| More valuable for leadership, research, or compliance-heavy roles | More valuable for technical, operational, and hands-on security roles |
| Often required for government and executive positions | Often required by employers to prove role-readiness (e.g., Pen Tester, SOC Analyst) |
| Expensive upfront but long-term investment | Cost-effective and stackable along your career journey |
Certification, Degree—Or Both?
So which is better—certification or degree?
It depends on your goals, timeline, and learning style.
Ask yourself:
- Do I want to start working in cybersecurity within 6 months? → Consider a certification-first approach.
- Am I in it for the long haul with goals of management or government work? → A degree may be a wise investment.
- Do I want both credibility and flexibility in the job market? → Combine both for maximum impact.
A well-thought-out cybersecurity certification roadmap often includes a mix of:
- Foundational education (degree or equivalent knowledge)
- Stackable certifications aligned with career goals
- Continuous learning through labs, bootcamps, and specializations
Remember: In cybersecurity, learning is lifelong. Whether you earn a Bachelor’s in Cybersecurity or start with Security+ and work your way up to CISSP, the key is to keep moving forward. Stay aligned with the ever-evolving demands of the industry.
Conclusion: Navigating Your Cybersecurity Certification Roadmap with Confidence
Recap of Your Cybersecurity Certification Roadmap
Whether you are just beginning your journey or looking to specialize, the Cybersecurity Certification Roadmap offers a structured pathway to help you achieve your professional goals. We have covered, from beginner-friendly certifications like CompTIA ITF+ and Microsoft SC-900 to intermediate-level programs such as CEH and GSEC. Finally to advanced and niche credentials like CISSP, OSCP, and CRISC. This Cybersecurity Certification Roadmap helps you make informed, strategic choices.
Each certification aligns with specific roles. You select the right certification, if you are aiming to be a Cybersecurity Analyst, Penetration Tester, Security Engineer, or even a Chief Information Security Officer (CISO). The roadmap empowers you to match your skill level, interests, and goals with the right certifications. It ensures you are never lost in the vast and evolving cybersecurity landscape.
Encouragement to Take the Next Step
No matter your background—student, career switcher, or seasoned IT professional—the best time to start your cybersecurity journey is now. Define your career goals. Assess your current skills. Select the certification phase that aligns with your aspirations.
Remember: the cybersecurity field is not just growing, it is exploding with opportunity. Employers are actively seeking certified professionals who bring not only credentials but hands-on skills and a commitment to continuous learning.
Tip: Combine your certifications with practical labs, projects, and community involvement to truly stand out.
Related Read: 7 Proven Cybersecurity Certifications for Career Advancement Mastery
To dive deeper into some of the most recognized certifications in the industry, we highly recommend checking out our previous guide:
7 Proven Cybersecurity Certifications for Career Advancement Mastery
It breaks down top credentials, their advantages, and how they fit within your Cybersecurity Certification Roadmap. In addition, it gives you a strong starting point for certification selection and planning.
Frequently Asked Questions About the Cybersecurity Certification Roadmap
Q1: What is the best cybersecurity certification to start with?
The best beginner cybersecurity certification for most people is CompTIA Security+. It covers core security skills needed in entry-level jobs. Other great options include CompTIA ITF+ for absolute beginners and Microsoft SC-900 for those interested in cloud-based security. These are widely recognized and align perfectly with Phase 1 of the Cybersecurity Certification Roadmap.
Q2: How do I become a cybersecurity expert?
To become a cybersecurity expert, follow a step-by-step learning path:
- Start with beginner-level certifications (ITF+, Security+)
- Gain hands-on experience through labs, simulations, or internships
- Progress to intermediate and advanced certifications (like CEH, GSEC, CISSP, or OSCP)
- Stay updated with the latest trends and tools
- Consider combining your certifications with a cybersecurity degree or specialization
A Cybersecurity Certification Roadmap helps you systematically build skills from beginner to expert level.
Q3: Can I work in cybersecurity without a degree?
Yes, it is entirely possible to start a cybersecurity career without a formal degree, if you earn industry-recognized cybersecurity certifications and can demonstrate practical skills. Many employers value hands-on experience and credentials like Cisco CyberOps Associate, CompTIA Security+, and OSCP just as much as or even more than a degree.
Q4: How long does it take to get certified?
The time needed depends on the certification level and your background:
- Beginner certifications (ITF+, SC-900): 1–2 months
- Intermediate certifications (CEH, GSEC): 2–4 months
- Advanced certifications (CISSP, OSCP): 4–12 months
Using a Cybersecurity Certification Roadmap will help you estimate preparation time and plan efficiently.
Q5: How do I choose the right certification based on my career goals?
First, define your desired role like Pen Tester, Security Analyst, or Cloud Security Engineer. Then select certifications aligned to that path.
For example:
- Penetration testing: OSCP, CEH
- Risk management: CRISC
- Cloud security: CCSP
A Cybersecurity Certification Roadmap helps you make role-specific decisions at every career phase.
Q6: Are cybersecurity certifications better than a degree?
They serve different purposes. Certifications validate hands-on skills and can fast-track employment. Degrees provide foundational theory and long-term growth. Ideally, they complement each other. See our full breakdown in the “Certification vs Degree” section.
Q7: What are the top cybersecurity certifications for career growth?
Some of the best certifications for long-term career advancement include:
- CISSP – for leadership roles
- OSCP – for ethical hacking
- CCSP – for cloud security
- CRISC – for risk management
- CEH – for offensive security roles
These align with mid-to-senior-level positions in your Cybersecurity Certification Roadmap.
Q8: Do cybersecurity certifications expire?
Yes. Most certifications require renewal every 2–3 years. For example:
- CompTIA: Requires Continuing Education Units (CEUs)
- CISSP: Requires Continuing Professional Education (CPE) credits
- CEH: Requires periodic updates via EC-Council’s recertification process
Keeping certifications current ensures you are up-to-date with cybersecurity trends and tools.