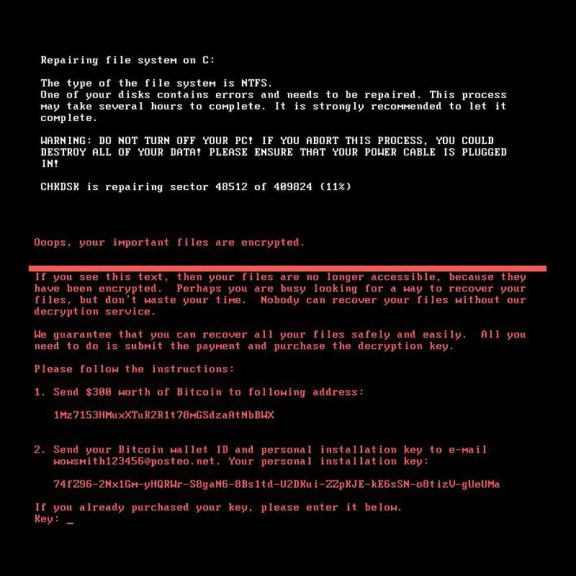
Petya Ransomware or Petrwap has infected several thousand computers since the service day. The malware encrypts user data and releases it allegedly against 300 dollar ransom. Experts believe, however, that Petya Ransomware is not a “real” Ransomware.
Until now, companies from the EU, Russia and Ukraine, where the first infections were observed, have been affected. German companies should also have become infected by this Petya Ransomware, including the Beiersdorf Group. Special attention was given to the infections of the Danish shipping company AP Moller-Maersk as well as to the international food group Mondelez and a hospital operator from Pittsburgh. The computers of the nuclear power plant in Chernobyl were also encrypted. There, radioactivity measurements had to be switched manually.
The extent of Petya Ransomware infections is similar to the WannaCry attack in May. The Ransomware took host computer networks of the railway and the British National Health Service into hostage. Security experts have now found that Petya, among other things, uses the same security vulnerability (EternalBlue) as WannaCry as an attack vector. This security exploit was originally developed by the NSA to gain access to Windows computers. The necessary software had been leaked last summer by the hacker group Shadow Brokers.
Meanwhile, the world is called upon to refuse the requested ransom of 300 dollars, which is to be passed on to an anonymous Bitcoin account. The German e-mail provider Posteo has already switched off the address to which the ransom is to be transferred.
It is not the first time that Petya Ransomware strikes. According to Alan Woodward, a security expert at the University of Surrey, Petya came early this year, as the BBC reports. However, experts from Kaspersky suggest that it is a completely new malware.
While at the outset Petya Ransomware was a malware with a criminal background, experts have moved away from this assessment. According to media reports, the payment mechanisms of the malware are set too superficially, to guarantee to a criminal behind a secure payment.
Each victim gets the same Bitcoin address, usually this is different in Ransomware attacks. In addition, it is unusual that only one e-mail address exists for the payment. Experts believe that Petya Ransomware is not a real blackmail malware, but is used as an IT weapon.
It is more than striking that Ukraine has become the main target, says Alex McGeorge of Immunity Inc. against business insiders. His company is specialized in state hacking. Ukraine was in the past repeatedly test target for Russian network attacks. McGeorge also suspected the Kremlin this time. It is also striking that another attack vector of Petya Ransomware specifically targets the update mechanism of a Ukrainian software.
Even before it came to the WannaCry attack in May, Windows released free security updates to protect users from it. However, not for older versions of Windows. After the WannaCry attack, however, Windows had also provided free updates for older versions. Whether the companies that have now been neglected to look at their networks to the latest security standards is still open. Obsolete security measures could, however, be the reason why the malware could attack the computers at all.