What is SSH or Secure Shell Protocol?
The Secure Shell Protocol or SSH is a cryptology network protocol for handling network services more securely over an unsecured network. Its most useful applications are Command Line Execution and Remote Sign-in. SSH applications are client-server architectures that are used to connect SSH clients with SSH servers.
It is a layered protocol suite comprising three principal hierarchical components: the transport layer, connection protocol, and authentication protocol. The transport layer is used for server authentication. The authentication protocol is used to validate the user to the server. And finally, connection protocol encrypts the logical communication channel.
In 1995, SSH was designed by Tatu Ylonen for Unix-like Operating Systems. Subsequent development of the protocols suite has happened in various developer groups. It was used as a replacement for Telnet and for unsecured remote Unix Shell protocols. SSH uses public-key cryptography to remove computer authentication.
Functions:
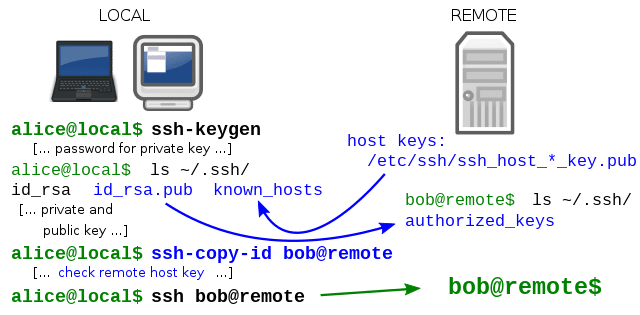
Generally, in Secure Shell Protocol, for encrypted network connection, both ends of the communication channels automatically generate a public and private key. Then the user needs to use the password for authentication. Besides, it so uses several other methodologies. There are three procedures employed in the data control strategies of the Secure Shell protocol. They are Symmetrical Security, Asymmetrical encryption, and Hashing.
When the user manually generates the public-private key, authentication is automatically performed when the key pair is created. Then, the secession automatically opened without the password prompt. Further, the public key is placed on all computers that allow access to the owner of the matching private key.
The authentication is based on the private key; therefore, the key is never transferred through the network during the authentication process. SSH, therefore, verifies whether the same person offering the public key also possesses the matching private key. In all Secure Shell Protocol versions, it is emphasized on verification of unknown public keys. To protect from the attackers, it won’t accept the public key without validation; therefore, it will verify the associated public keys with identities before approving them as valid.
The SSH encrypts data and not FTP. FTP sends data in an unencrypted format. Since SSH provides strong encryption and integrity protection, it is slower than FTP.
Authentication Process:
In OpenSSH key management, the list of authorized public keys is generally stored in the user’s home directory to help him log in remotely in the system file ~/.ssh/authorized_keys. This public Key file will be honored if and only if it is rewriteable by the owner and root alone. When the public key is available at the remote end, and its matching key is available on the local end, typing the password is not required to log in.
But for security purposes, the private key itself can be locked with a passphrase. Normally the private key can be looked for in specific places, and its path can be specified as command line settings with the option –i for ssh. ssh-keygen is a standard component tool of the Secure Shell protocol. ssh-keygen utility always produces the public and private keys in pairs.
Secure Shell Protocol can also support password-based authentication that is encrypted by automatically generated keys. In man in the middle attack case, the attacker could imitate the server side, ask for the password, and get it. But it is only possible when two sides have never authenticated before since the Secure Shell Protocol always remembers the key that the server side previously used. Normally the Secure Shell Protocol always raises the warning while accepting the key of a new or unknown server. Further, password authentication can be disabled from the server side.
The Internet Assigned Numbers Authority (IANA) assigned TCP port 22, SCTP Port, and UDP port 22 for SSH protocol. The Internet Assigned Numbers Authority assigned TCP port 22 exclusively for SSH servers as one of the well-known ports.
Uses of Secure Shell Protocol:
SSH is normally used for logging into a remote system to execute commands. It uses the client-server model.
- It is used in tunneling to move data from one network to another
- It is used in Port Forwarding or Port Mapping. Port Forwarding permits Remote Computers to connect to a specific computer or utilize service within the Local area network.
- Secure Shell Protocol employed in TCP ports
- It is used in X11 connections of Windows systems. X11 uses a client-server model
- SSH can transfer files using the associated SSH File transfer protocol.
- It can be used in Secure Copy (SCP) protocol.
- In Cloud computing, SSH is important for solving connectivity problems.
- It helps to avoid the security issues of exposing cloud-based virtual machines on the internet.
- SSH Tunnel provides a more secured path over the internet through the firewall to a virtual machine.
- The SSH client program establishes the connection to an SSH daemon or sshd, a background process. It accepts remote connections.
Other Uses of SSH:
Further, Secure Shell Protocol can be employed in many applications across many platforms, including Linux, BSD, macOS, Windows, and Solaris
- Mainly used to login to a shell on a remote host by replacing Telnet and rlogin
- Used to execute a single command on a remote host by replacing rsh
- It helps to set up automatic passwordless automatic login to a remote server
- Together with rsync, it can backup, copy, or mirror files more efficiently and more securely
- It can be employed as forwarding a port
- It can be used for tunneling
- Use it as a full-fledged encrypted VPN in OpenSSH servers and SSH client
- Use it to forward X windows system from a remote host, even through multiple intermediate hosts
- It can be used to browse the web through an encrypted proxy connection with an SSH client, which supports the SOCKS protocol.
- Mount a directory on a remote server more securely as a file system on a local computer system using SSHFS
- It can be used to automate the remote monitoring and management servers
- It helps in the development of an embedded device or on a mobile that supports SSH
- For more secured file transfer protocols
Uses of SSH in File Transfer Protocols:
SSH protocols are used in a few file transfer mechanisms.
Secure Copy Protocol evolved from RCP protocol over SSH. SCP or secure copy 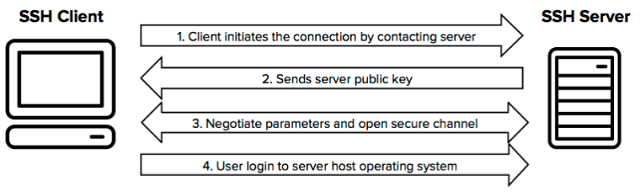
Rsync is a more efficient file-sharing protocol that runs over an SSH connection. Rsync is a utility used for transferring and synchronizing files between computer systems and a storage drive across networked computer systems. It compares modification times and sizes of the files while doing.
SSH File Transfer Protocol, an extension of SSH, is a secure alternative to FTP. Internet Engineering Task Force designed it. The Secured File Transfer Protocol (SFTP) is a network protocol that assists in file access, file transfer, and file management over a reliable, secured data stream.
FISH, files transferred over shell protocol evolved from SSH. Therefore, FISH needs SSH or RSH implementation on the server side as a set of standards.
FASP (Fast Adaptive and Secure Protocol use SSH for access control and UDP ports for data transfer. It is a proprietary data transfer protocol. FASP is owned by IBM and was developed by Aspera. It does not suffer much loss of throughput as TCP, which has high packet loss and high latency. The maximum transmission rate is chosen to match and not to exceed the channel bandwidth to minimize packet loss. In addition, it has a built-in security mechanism that does not affect the transmission speed.
SSH Architecture:
SSH doesn’t use either Transport Layer Security (TLS) protocol or Secure Socket Layer (SSL).
Secure Shell Protocol is a layered architecture with three separate components: the Transport Layer, User Authentication Layer, and Connection Layer.
The Transport Layer:
The Transport Layer (Request for Comments RFC) uses the transmission control protocol of TCP reserving port number 22 as a listening port for the server. Transport Layer handles initial key exchange and server authentication, sets up encryption, compression, and integrity verification. This upper layer works as an interface for sending and receiving plaintext packets. The packet size may be up to 32,768 bytes each, but the implementation can increase size. The transport layer arranges for key re-exchange. Message Authentication Code (MAC) algorithms are employed in data integrity check.
User Authentication Layer:
The user Authentication Layer handles client authentication and provides a suite of algorithms for authentication. Its authentication is client driven. It is SSH client prompting. The server merely responds to authentication requests.
The authentication request methods are the following:
Password: It is straightforward password authentication. And it also allows the user to change the password.
Public key authentication: The method for public key-based authentication supports DSA, ECDSA, or RSA Key pairs with other implementations.
Keyboard Interactive: Keyboard Interactive is a novel method where the server sends one or more prompts to enter data, and clients display them and send back responses sent by the user who needs to input one-time password authentication such as SecurID or S/Key. It uses some OpenSSH configurations.
GSSAPI Authentication: It is the method that provides an extensible scheme to perform SSH authentication using Kerberos5 or NTLM, providing single sign-on method to SSH sessions. These are SSH implementations.
The Connection Layer:
The SSH Connection Protocol creates distinct data streams or logical channels from the single client/server connection. The connection layer defines the channel concept, channel requests, and global requests. In addition, it establishes the SSH service provided. Any Single SSH connection can be multiplexed into multiple logical channels simultaneously. Each channel sends and receives data bi-directionally. The Channel requests are used to relay out of band channel Specific data. Each channel performs its own flow control using the receiving window size. SSH client requests a server-side port to be forwarded using a global request.
This architecture provides flexibility and allows the use of SSH for various purposes beyond a secure shell. The function of the transport layer is similar to Transport Layer Security. The User Authentication layer is highly extensible with custom authentication methods. Finally, the connection layer provides multiplex many secondary sessions into a single SSH connection.
How Secured is SSH Protocol?
The SSH protocol security is imperfect; we can easily protect them from illegal access since we know the flaws. With Standard security precautions, Secure Shell Protocol is firmly secured. However, it has some flaws; let us discuss them here. Normally SSH servers are attacked by brute force attacks. If the attackers gain access to the server, they can easily access the root account by using privilege escalation. Furthermore, when the attacker gains access to an SSH key, he can easily gain access to all other keys stored on the device. Further, if he can get a couple of keys, then he can gain remote user access to the entire network system.
Though SSH keys are more secure than passwords, poor SSH key management poses a significant risk. The exposed SSH ports are another potential security threat. The exposed ports can be attacked with malware programs with IoT devices, and it will give them backdoor access to the local network.
SSH is Vulnerable When the Following Happens:
Inadequate SSH key tracking: Big companies that handle large numbers of servers may have a vast number of SSH keys. Therefore they may lose track of some of them. If the hackers put their hands on them, then they can easily get access to those keys as well as the servers.
Frequent sharing of SSH keys: Since the hackers only need a couple of keys to get remote access, key sharing is strictly monitored in bigger organizations.
Static SSH keys and embedded keys: The administrators won’t change the keys routinely for fear of forgetting them. Therefore it creates a lot of static keys. They can give potential entry to cyber criminals. Besides, keys embedded within applications and scripts can also become static. Because of the codes, most administrators avoid changing them periodically.
Conclusion:
Though the Secure Shell Protocol is a highly complex network protocol, all communication between the client and the server is encrypted. Because of these safety features, it is widely used and has greater popularity. Though it has its own flaws, it is much better than other authentication procedures. This blog post helps you to understand what SSH protocol is and how Secure Shell Protocol works, what it is used for, and how the user can use it safely.